Hacking APIs: Authentication & Authorization Attacks

As you know, API/Endpoints are called from many types of devices to receive information. In terms of security, your API/Endpoints must to be aware who is receiving this information, for this, there are two process authentication and authorization, this article will show you how to attack/test the authentication process.
What does Authentication means?
In this process object verify the subject’s identity through something that subject has, for example credentials.
I sent credentials using POST /identity/api/auth/login and server response 401.

First sent the request to Intruder, select password field and click on add, this field will be attack using a common password.

Go to the payload and select your favorite list of common passwords.

Attack the API/Endpoint, you need to see Status code in order to identify the right password for this user, and get JWT Token

Another good example to attack API/Endpoint authenticated, is using wfuzz, see image below:

Besides authentication process successfully, we got the token and try to break it, send the request to the “Sequencer”, select the token’s value in order to define start and end of the parameter that will be analyzed and click on “OK”

Click on “Start live capture” after get some a “few” token press Analyze now, in this case, the token is not easy to break or predict.

BOLA (Broken Object Level Authorization)
You can manipulate the object id in order to get information from different object(authenticated users), you have a better explanation below:
First thing that we can try is get data or information from other user or vehicle in this case, so go to dashboard and click on “Refresh Location”, see image below:

Through Burp suite we can see all requests and their response, and get “carID” is the same in the HTTP request, but What happend if I try to change for other carID that isn’t mine?

We need to get others “carID” for it, go to “Community” and see all post, using burp suite you can see “a lot of unnecessary data”, there are some “carID”.

Send the request to repeater and change the vehicle’s carID for other and send it, if everything is ok (for us, not for developers), we will able to see location from other car, that is BOLA (Broken Object Level Authorization)

We can see other great example of BOLA, getting information from other authenticated user, click on Contact Mechanic, and write down the require information and click on “Send Service Request”

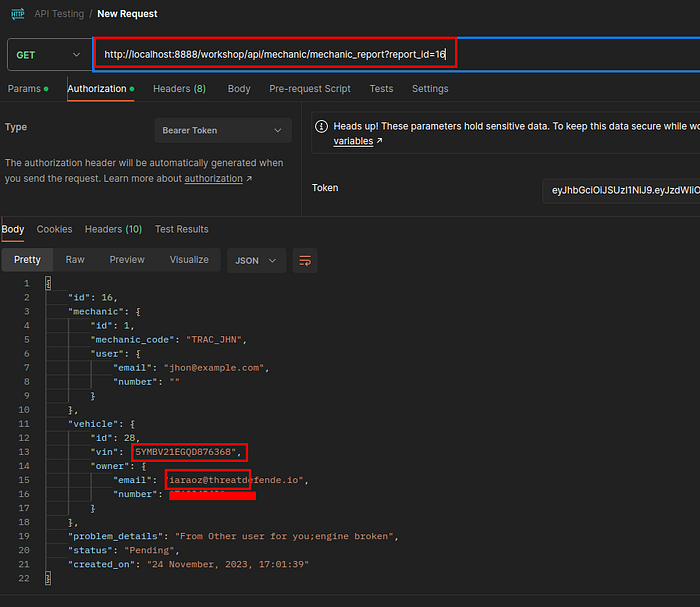
Send the request and see the server response, we can see a specific variable in order to get one report, but this report is for this current user, this user should be unable to see other user’s report.

Open Postman, copy and paste the request in order to call the endpoint /api/mechanic/mechanic_report?report_id, don’t forget your bearer token, send the request and see the result, report from another authenticated user.

BFLA (Broken Function Level Authorization)
If BOLA is related to get data from other authenticated user, BFLA is related to do some actions not allowed for the current user, check below:
In this example, I am going to show you how to request service for another authenticated user’s car. In order to do this, you need other VIN, see image “carIDs from others vehicle” from BOLA section and get VIN, use this endpoint /workshop/api/merchant/contact_mechanic, and replace the current user’s vin with the VIN from other user and sent the request.

Using postan, we can see the request service was assigned another user, from user iaraoz@mail.com -> iaraoz@threatdefenderio
And that’s it, see you folks!)
